We will start this example from the very beginning.
We'll create a certificate, a keystore and will perform all the different steps needed to get us started (using Keytool & OpenSSL)
Then we'll configure WebLogic to use that keystore.
Once a browser is able to access WebLogic, we will configure Apache to use SSL with WebLogic.
1 - Create a CSR & a keystore
In order to create these components, the tool used is Keytool from Sun. You have it in any JVM install :
For me it's : %BEA_HOME%\jdk160_05\bin\keytool.exe
For this example, as I'm lazy sometimes, I'm going to use Keytool UI, which is a graphical version of keytool, as its name tells.
First, let's create a sample and empty JKS. (JKS stands for Java KeyStore)

In this example, the password used is "weblogic".
Then just create a CSR (Certificate Signing Request)
Specify the previously created JKS and the algorithm to use :

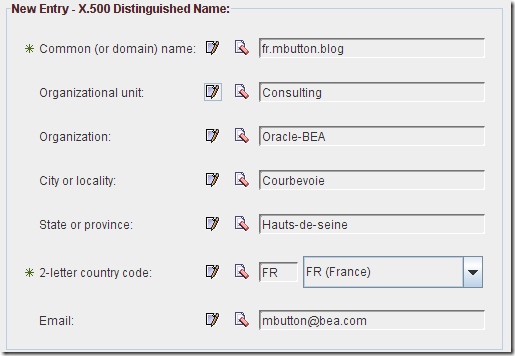
Fill in the different fields, as you would with Keytool :
The creation should result in a small popup :

Viewing the content of the keystore

I used the following for the private key :
- alias : privatekey
- password : weblogic
2 - Configure WebLogic to use the previously created keystore
That's the easy part :)
Start your server and check that you have SSL enabled.

Then just change the identity of the server to point towards our keystore.

Here are the different options proposed. In our example, the option that best fits our need is "Custom identity & Java Standard Trust".
"Custom Identity" means we're using our own keystore and "Java Standard Trust" means we use the truststore from the JDK.
(%BEA_HOME%\jdk160_05\jre\lib\security\cacerts)
A truststore is a keystore containing all the trusted certificates.
You may print the truststore, just to see what's inside :

You can see that Verisign, Thawte and many other CA (Certificate Authorities) are listed.

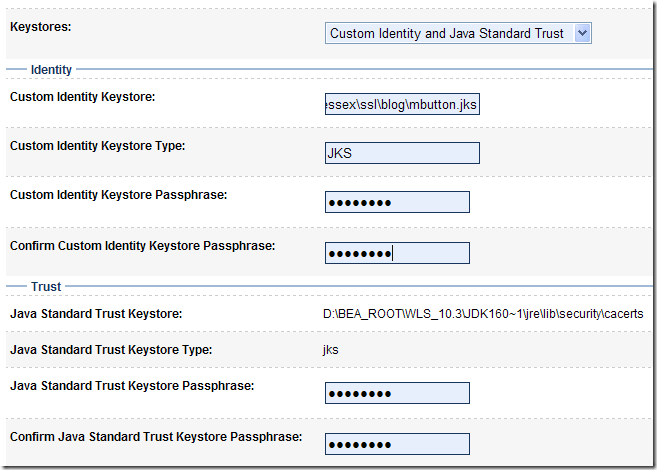
We only have to specify the keystore we created, the type which is JKS and the password.
As for the Trust, just type the default password, which is "changeit".
A quick look in the WLS console shows :
<10 nov. 2008 23 h 47 CET> <Error> <WebLogicServer> <BEA-000297>
<Inconsistent security configuration, weblogic.management.configuration.ConfigurationException:
Cannot retrieve identity certificate and private key on server AdminServer, because the keystore entry alias is not specified.>
<10 nov. 2008 23 h 47 CET> <Error> <Server> <BEA-002618>
<An invalid attempt was made to configure a channel for unconfigured protocol "Cannot retrieve identity certificate
and private key on server AdminServer, because the keystore entry alias is not specified.".>
It's because we didn't supply the private key alias.

Just type the alias (privatekey) and the password (weblogic) and save.
This time, WLS seems to be happier :
<10 nov. 2008 23 h 52 CET> <Notice> <Security> <BEA-090171>
<Loading the identity certificate and private key stored under the alias privateKey from the JKS keystore
file D:\BEA_ROOT\user_projects\domains\essex\ssl\blog\mbutton.jks.>
<10 nov. 2008 23 h 52 CET> <Notice> <Security> <BEA-090169>
<Loading trusted certificates from the jks keystore file D:\BEA_ROOT\WLS_10.3\JDK160~1\jre\lib\security\cacerts.>
<10 nov. 2008 23 h 52 CET> <Notice> <Server> <BEA-002613>
<Channel "DefaultSecure" is now listening on 192.168.1.4:7002 for protocols iiops, t3s,
CLUSTER-BROADCAST-SECURE, ldaps, https.>
<10 nov. 2008 23 h 52 CET> <Notice> <Server> <BEA-002613>
<Channel "DefaultSecure[1]" is now listening on 127.0.0.1:7002 for protocols iiops, t3s,
CLUSTER-BROADCAST-SECURE, ldaps, https.>
Let's try to access the console using the secure port (7002).
A popup shows up :

Just some warning message saying that the certificate has been emitted by someone I don't trust
and that the certificate name doesn't match the site name.

It works.
3 - Display the certificate presented by WebLogic
To display the certificate, we've got two possibilities :
Click the lock in the browser window and use the built-in functionality to display the certificates.

Or use OpenSSL, which is the method I prefer.
C:\Documents and Settings\mbutton>openssl s_client -connect localhost:7002
Loading 'screen' into random state - done
CONNECTED(00000728)
depth=0 /emailAddress=mbutton@bea.com/C=FR/ST=Hauts-de-seine/L=Courbevoie/O=Oracle-BEA/OU=Consulting/CN=fr.mbutton.blog
verify error:num=18:self signed certificate
verify return:1
depth=0 /emailAddress=mbutton@bea.com/C=FR/ST=Hauts-de-seine/L=Courbevoie/O=Oracle-BEA/OU=Consulting/CN=fr.mbutton.blog
verify return:1
---
Certificate chain
0 s:/emailAddress=mbutton@bea.com/C=FR/ST=Hauts-de-seine/L=Courbevoie/O=Oracle-BEA/OU=Consulting/CN=fr.mbutton.blog
i:/emailAddress=mbutton@bea.com/C=FR/ST=Hauts-de-seine/L=Courbevoie/O=Oracle-BEA/OU=Consulting/CN=fr.mbutton.blog
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICtzCCAiCgAwIBAgIESRixbTANBgkqhkiG9w0BAQUFADCBnzEeMBwGCSqGSIb3
DQEJARYPbWJ1dHRvbkBiZWEuY29tMQswCQYDVQQGEwJGUjEXMBUGA1UECAwOSGF1
dHMtZGUtc2VpbmUxEzARBgNVBAcMCkNvdXJiZXZvaWUxEzARBgNVBAoMCk9yYWNs
ZS1CRUExEzARBgNVBAsMCkNvbnN1bHRpbmcxGDAWBgNVBAMMD2ZyLm1idXR0b24u
YmxvZzAeFw0wODExMTAyMjEwNTNaFw0xMTExMTAyMjEwNTNaMIGfMR4wHAYJKoZI
hvcNAQkBFg9tYnV0dG9uQGJlYS5jb20xCzAJBgNVBAYTAkZSMRcwFQYDVQQIDA5I
YXV0cy1kZS1zZWluZTETMBEGA1UEBwwKQ291cmJldm9pZTETMBEGA1UECgwKT3Jh
Y2xlLUJFQTETMBEGA1UECwwKQ29uc3VsdGluZzEYMBYGA1UEAwwPZnIubWJ1dHRv
bi5ibG9nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCE4Eu/kWbTfjFQNWzm
YEGLEO8Mp7SY9R2d4MpZTCAPdS7DSjY1AsJMlTDxomsWAKdU/UaQuf0quyuO4oiM
7IxFMTHXEZ1TgXMUgHGgNYnkQIivcbskUFJuPUoYHW6mR9rlIkkVSkTPUVWaGvzt
gubEQhUvc1ndt8bpQRmnnOkZgQIDAQABMA0GCSqGSIb3DQEBBQUAA4GBAEEpAwNF
Fa21wGzoBk7WzQkHuWKfY3D2mCuON+u9GWHxrQoDG+u6i4LyY/5DK9IMrs5tzq7u
9htJAryKJVMpHH05Nb0Bq9ZENylHLb8nIeAZP6A8w1WVb4xfRC1KAz7HLcA3xlBw
9+RanPitwglr9GX6teINf8te3m7hVS1wC3Hg
-----END CERTIFICATE-----
subject=/emailAddress=mbutton@bea.com/C=FR/ST=Hauts-de-seine/L=Courbevoie/O=Oracle-BEA/OU=Consulting/CN=fr.mbutton.blog
issuer=/emailAddress=mbutton@bea.com/C=FR/ST=Hauts-de-seine/L=Courbevoie/O=Oracle-BEA/OU=Consulting/CN=fr.mbutton.blog
---
No client certificate CA names sent
---
SSL handshake has read 829 bytes and written 306 bytes
---
New, TLSv1/SSLv3, Cipher is RC4-MD5
Server public key is 1024 bit
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1
Cipher : RC4-MD5
Session-ID: 48076FBB49156AD46E8B1DE5C6761319
Session-ID-ctx:
Master-Key: 0FE8F6A1A4A498FBE9832D7BE2FD999C2DA9C697F1311F6DE39A461293AD643E12DB8089828082581352D8FD5FF8E310
Key-Arg : None
Start Time: 1226358012
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
---
The section in red represents the certificate presented by the server.
ASCII delimited by "-----BEGIN CERTIFICATE-----" & "-----END CERTIFICATE-----" means it's a PEM.
We need to isolate it. Then just copy it in a file and name it "server.pem" for instance.
4 - Configure Apache SSL to access WebLogic
First, copy the apache plugin in the apache modules directory.
%BEA_ROOT%\wlserver_10.3\server\plugin\win\32\mod_wl_22.so
towards %APACHE_HOME%\modules
In your httpd.conf, add the following lines to have a clean and separate configuration for WebLogic.
############## WLS 10 Proxy Plugin
<IfModule !mod_weblogic.c>
LoadModule weblogic_module modules/mod_wl_22.so
</IfModule>
<IfModule mod_weblogic.c>
# Config file for WebLogic Server that defines the parameters
Include conf/weblogic.conf
</IfModule>
These few lines include the file weblogic.conf.
This file looks like :
<IfModule mod_weblogic.c>
<Location /console>
SetHandler weblogic-handler
WebLogicHost localhost
WebLogicPort 7002
# SSL
SecureProxy ON
WLProxySSL ON
RequireSSLHostMatch false
TrustedCAFile D:\BEA_ROOT\user_projects\domains\essex\ssl\blog\server.pem
EnforceBasicConstraints false
# DEBUG
WLLogFile D:\BEA_ROOT\user_projects\domains\essex\ssl\blog\wlproxy.log
Debug ALL
DebugConfigInfo ON
</Location>
</IfModule>
As you may have noticed, the "TrustedCAFile" is the full path towards our server certificate (the one we got from OpenSSL !)
For more information about configuring WebLogic plugin, http://edocs.bea.com/wls/docs100/plugins/apache.html
Then accessing the console through the following URL : http://localhost/console shows in the wlproxy.log :
Tue Nov 11 00:08:43 2008 <502412263585231>
================New Request: [GET /console HTTP/1.1] =================
Tue Nov 11 00:08:43 2008 <502412263585231> INFO: SSL is configured
Tue Nov 11 00:08:43 2008 <502412263585231> SSL Main Context not set. Calling InitSSL
Tue Nov 11 00:08:43 2008 <502412263585231> INFO: SSL configured successfully
Tue Nov 11 00:08:43 2008 <502412263585231> Using Uri /console
Tue Nov 11 00:08:43 2008 <502412263585231> After trimming path: '/console'
Tue Nov 11 00:08:43 2008 <502412263585231> The final request string is '/console'
Tue Nov 11 00:08:43 2008 <502412263585231> Host extracted from serverlist is [localhost]
Tue Nov 11 00:08:43 2008 <502412263585231> Initializing lastIndex=0 for a list of length=1
Tue Nov 11 00:08:43 2008 <502412263585231> getListNode: created a new server node: id='localhost:7002' server_name='localhost', port='80'
Tue Nov 11 00:08:43 2008 <502412263585231> attempt #0 out of a max of 5
Tue Nov 11 00:08:43 2008 <502412263585231> Trying a pooled connection for '127.0.0.1/7002/7002'
Tue Nov 11 00:08:43 2008 <502412263585231> getPooledConn: No more connections in the pool for Host[127.0.0.1] Port[7002] SecurePort[7002]
Tue Nov 11 00:08:43 2008 <502412263585231> general list: trying connect to '127.0.0.1'/7002/7002 at line 2619 for '/console'
Tue Nov 11 00:08:43 2008 <502412263585231> New SSL URL: match = 0 oid = 22
Tue Nov 11 00:08:43 2008 <502412263585231> Connect returns -1, and error no set to 10035, msg 'Unknown error'
Tue Nov 11 00:08:43 2008 <502412263585231> EINPROGRESS in connect() - selecting
Tue Nov 11 00:08:43 2008 <502412263585231> Setting peerID for new SSL connection
Tue Nov 11 00:08:43 2008 <502412263585231> 7f00 0001 5a1b 0000 ....Z...
Tue Nov 11 00:08:43 2008 <502412263585231> Local Port of the socket is 1782
Tue Nov 11 00:08:43 2008 <502412263585231> Remote Host 127.0.0.1 Remote Port 7002
Tue Nov 11 00:08:43 2008 <502412263585231> general list: created a new connection to '127.0.0.1'/7002 for '/console', Local port:1782
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from clnt:[Accept]=[image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, ...
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from clnt:[Accept-Language]=[fr]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from clnt:[Accept-Encoding]=[gzip, deflate]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from clnt:[User-Agent]=[Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; ...
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from clnt:[Host]=[localhost]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from clnt:[Connection]=[Keep-Alive]
Tue Nov 11 00:08:43 2008 <502412263585231> URL::sendHeaders(): meth='GET' file='/console' protocol='HTTP/1.1'
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[Accept]=[image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, ...
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[Accept-Language]=[fr]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[Accept-Encoding]=[gzip, deflate]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[User-Agent]=[Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; ...
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[Host]=[localhost]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[Connection]=[Keep-Alive]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[WL-Proxy-SSL]=[true]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[WL-Proxy-Client-IP]=[127.0.0.1]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[Proxy-Client-IP]=[127.0.0.1]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[X-Forwarded-For]=[127.0.0.1]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[X-WebLogic-KeepAliveSecs]=[30]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to WLS:[X-WebLogic-Force-JVMID]=[unset]
Tue Nov 11 00:08:43 2008 <502412263585231> INFO: Certificate validation succeeded
Tue Nov 11 00:08:43 2008 <502412263585231> INFO: Negotiated to cipher: 3
Tue Nov 11 00:08:43 2008 <502412263585231> SSLWrite sent 782
Tue Nov 11 00:08:43 2008 <502412263585231> SSLWrite completed, sent 782
Tue Nov 11 00:08:43 2008 <502412263585231> Reader::fill() SSLRead success, read: 202
Tue Nov 11 00:08:43 2008 <502412263585231> URL::parseHeaders: CompleteStatusLine set to [HTTP/1.1 302 Moved Temporarily]
Tue Nov 11 00:08:43 2008 <502412263585231> URL::parseHeaders: StatusLine set to [302 Moved Temporarily]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from WLS:[Date]=[Mon, 10 Nov 2008 23:08:43 GMT]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from WLS:[Transfer-Encoding]=[chunked]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from WLS:[Location]=[https://localhost/console/]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from WLS:[X-WebLogic-JVMID]=[-353258681]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs from WLS:[X-Powered-By]=[Servlet/2.5 JSP/2.1]
Tue Nov 11 00:08:43 2008 <502412263585231> parsed all headers OK
Tue Nov 11 00:08:43 2008 <502412263585231> sendResponse() : r->status = '302'
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to client (reset):[Date]=[Mon, 10 Nov 2008 23:08:43 GMT]
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to client (reset):[Location]=[https://localhost/console/]
Tue Nov 11 00:08:43 2008 <502412263585231> for 127.0.0.1/7002/7002, updated JVMID: -353258681
Tue Nov 11 00:08:43 2008 <502412263585231> Hdrs to client (reset):[X-Powered-By]=[Servlet/2.5 JSP/2.1]
Tue Nov 11 00:08:43 2008 <502412263585231> Reader::fill() SSLRead success, read: 255
Tue Nov 11 00:08:43 2008 <502412263585231> Reader::fill() SSLRead success, read: 8
Tue Nov 11 00:08:43 2008 <502412263585231> canRecycle: conn=1 status=302 isKA=1 clen=-1 isCTE=1
Tue Nov 11 00:08:43 2008 <502412263585231> closeConn: pooling for '127.0.0.1/7002'
Tue Nov 11 00:08:43 2008 <502412263585231> request [/console] processed sucessfully..................
And if we set a bad certificate name, restart Apache, an access to the same URL shows :
Tue Nov 11 00:09:59 2008 <340812263585991>
================New Request: [GET /console HTTP/1.1] =================
Tue Nov 11 00:09:59 2008 <340812263585991> INFO: SSL is configured
Tue Nov 11 00:09:59 2008 <340812263585991> SSL Main Context not set. Calling InitSSL
Tue Nov 11 00:09:59 2008 <340812263585991> ERROR: SSL initialization failed
So this it ...
Hope it was clear and useful. Anyway, here are just the main lines. Don't go in production with such a configuration :)
(even if it's not worst than using WebLogic DemoTrust & DemoCertificates ...)





























